Welcome to EASM-UK, your trusted source for all your External Attack Surface Management requirements. We are dedicated to protecting your digital assets and ensuring your online safety.
External Attack Surface Management (EASM) refers to the process of identifying, assessing, and mitigating the potential points of attack on an organization's external-facing assets, such as networks, systems, applications, and online presence. The "attack surface" refers to all the points and methods by which an attacker might try to gain unauthorized access to an organization's resources.
At EASM-UK we help our clients by conducting analysis of the Surface, Deep and Dark do deliver the following key areas of EASM:
-
Asset Discovery: Identifying and cataloging all external-facing assets, including websites, applications, servers, cloud instances, network infrastructure, Certiface details and Shadow IT.
-
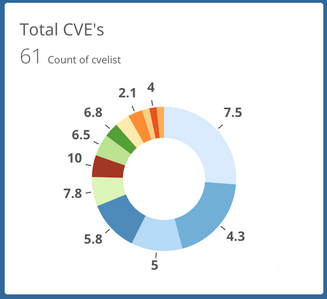
Vulnerability Assessment: Conducting regular assessments to identify vulnerabilities in the external-facing assets. This involves scanning for known vulnerabilities and weaknesses that could be exploited by attackers.
-
Attack Surface Mapping: Creating a comprehensive map of the organization's external attack surface, including understanding how various assets are interconnected and the potential attack paths that could be exploited.
-
Brand and Domain Impersonations: Discover
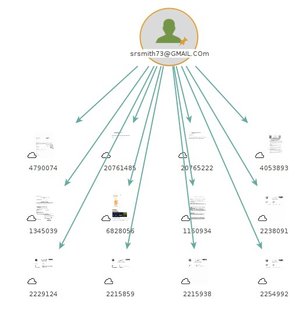
Domain and brand impersonations which are tactics used by malicious actors to deceive individuals or organizations by mimicking legitimate domains or brands.
- Compromised Credential & Data Leaks: Discover
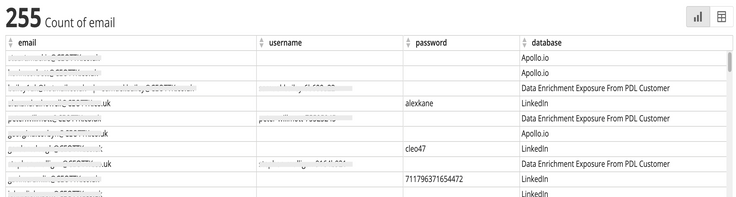
Compromised credentials (such as usernames and passwords) that have been stolen, leaked, or otherwise obtained by unauthorized individuals or parties.
-
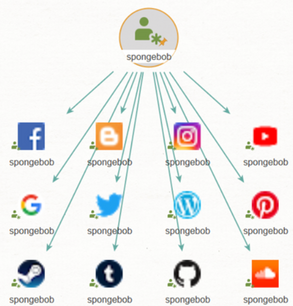
Social Media Attack Surface: Social media platforms often serve as an extension of an organization's online presence. Companies use social media for branding, customer engagement, and marketing. Any social media account or page associated with the organization becomes part of the external attack surface. Attackers may exploit vulnerabilities in these accounts or use them as entry points for broader attacks.
-
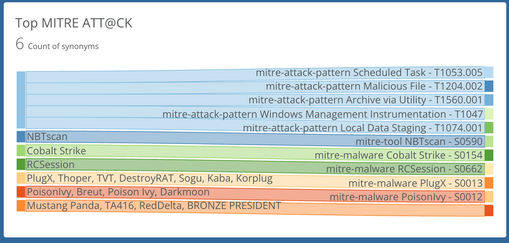
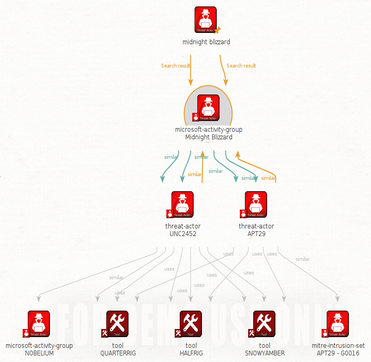
Threat Intelligence & Threat Actor Reporting: Incorporating threat intelligence to understand current and emerging threats and Threat Actor Groups that may impact the external attack surface. This helps in proactively addressing potential risks.
What is EASM?
SERVICES
External Attack Surface Management
Consultanty
At EASM-UK, we extend a warm welcome to those seeking assistance in cyber security. Our focus is on external attack surface management, ensuring your online presence remains secure.
EASM Reporting
At EASM-UK, we specialize in ensuring the security of your digital infrastructure. Our comprehensive cyber security services include conducting thorough assessments to determine your external attack surface posture. With our advanced tools and expertise, we provide detailed reports that highlight potential vulnerabilities and recommend strategies to strengthen your defenses. Trust EASM-UK to safeguard your organization from external threats and maintain the integrity of your digital assets.
OUR STORY
Building Cyber Security through Expert Consultation
With 15 years of cyber security experience, EASM-UK is committed to making the internet a safer place for our clients. Our team of experts is dedicated to protecting your data and preventing cyber threats. From safeguarding your sensitive information to implementing robust security measures, we provide comprehensive solutions to ensure your peace of mind online. Trust EASM-UK for all your cyber security needs.
As the threat landscape continues to evolve, we have grown and adapted to meet the ever-changing needs of our clients. Our Consulting Firm is now a trusted partner for businesses in various industries. We provide comprehensive guidance and solutions to mitigate risks and strengthen security posture. With an unwavering commitment to excellence, we strive to build secure futures for all our clients.
WHY WORK WITH US
Securing Your World
Strategic Guidance
Our consulting firm provides strategic guidance to help your business achieve ideal security posture.
Expert Analysis
With our expert analysis, we identify potentioal weaknesses within your internet facing assets that could be exploited by threat actors.
Custom Solutions
We offer tailored solutions to meet your specific needs, ensuring maximum efficiency and effectiveness.
TESTIMONIALS
Satisfied Clients Speak Out
Jacob Anderson
CTO
Working with EASMUK has been a game-changer for us. Their expertise and guidance have helped us achieve a far more secure working environment.
Susan Green
CISO
We're extremely pleased with the exceptional service provided by EASMUK. Their EASM Reports and
Recommendations have significantly improved our operational efficiency.
Dave Patterson
Cyber Security Director
EASMUK's insights into our Cyber Security posture has revolutionized our business. These guys really know their stuff!
GET IN TOUCH